Integration with Github Actions¶
Introduction¶
Integrating Licensight Scan into your CI/CD pipeline helps you automatically scan every code change for open-source vulnerabilities, license risks, and policy violations. This ensures continuous monitoring and helps catch issues early in the development process.
Prerequisites¶
Define these secrets and variables in the GitHub repository.
Configure variables¶
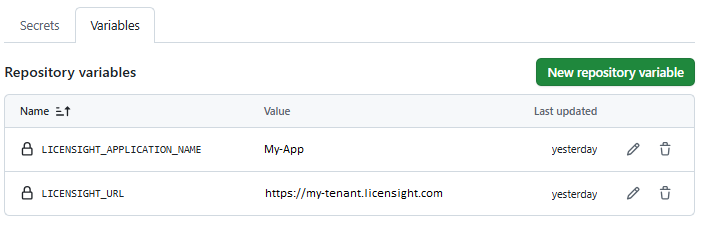
Go to: Settings > Security > Secrets and variables > Variables
Variable |
Description |
|---|---|
LICENSIGHT_APPLICATION_NAME |
The name of the application in Licensight platform. |
LICENSIGHT_URL |
Licensight platform endpoint (e.g., https://my-tenant.licensight.com) |
Configure secrets¶
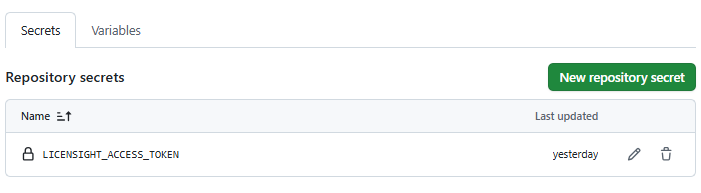
Go to: Settings > Security > Secrets and variables > Secrets
Secrets |
Description |
|---|---|
LICENSIGHT_ACCESS_TOKEN |
Your Licensight access token. Please refer to Creating an access token for detailed instructions. |
Licensight Integration for GitHub¶
For details on the parameters of Licensight Scan, refer to Using Licensight Scan. Create a workflow file:
.github/workflows/scan.yml
Scan Pull Requests with GitHub Actions¶
name: scan
on:
pull_request:
branches:
- '*'
jobs:
licensight:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v4
- name: Licensight scan for the Pull Request
env:
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
run: |
curl -O https://licensight.s3.eu-central-1.amazonaws.com/latest/linux/licensight-scan
chmod +x ./licensight-scan
./licensight-scan generate \
-d . \
-a "${{ vars.LICENSIGHT_APPLICATION_NAME }}" \
-e ${{ vars.LICENSIGHT_URL }} \
-at ${{ secrets.LICENSIGHT_ACCESS_TOKEN }} \
-b ${{ github.head_ref }} \
-dpr true
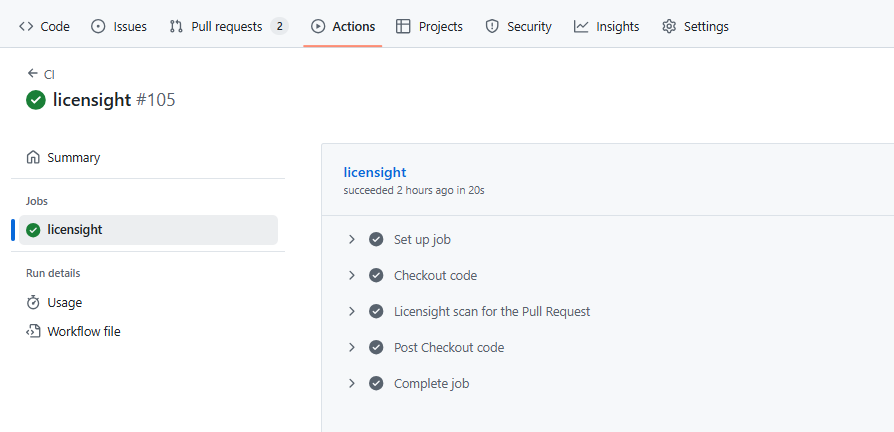
When a new PR is created, the workflow will:
- Automatically run the scanner on the changed code:
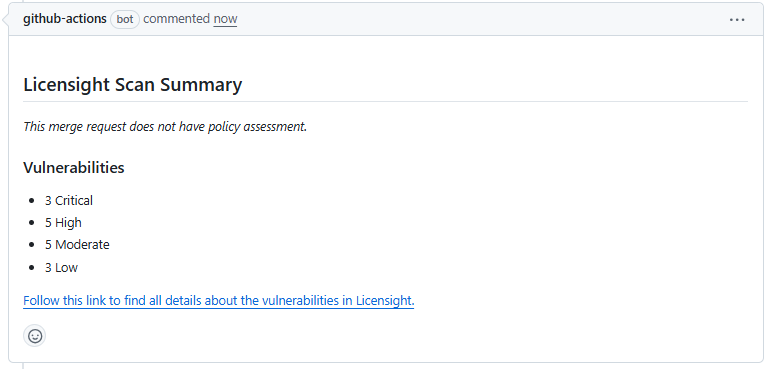
- Decorate the Pull Request with scan results:
Scan on Default Branch¶
This GitHub Actions below trigger Licensight every time code merge to default branch
name: scan
on:
push:
branches:
- '*'
jobs:
licensight:
if: github.ref_name == github.event.repository.default_branch
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v4
- name: Licensight scan for default branch
run: |
curl -O https://licensight.s3.eu-central-1.amazonaws.com/latest/linux/licensight-scan
chmod +x ./licensight-scan
./licensight-scan generate \
-d . \
-a "${{ vars.LICENSIGHT_APPLICATION_NAME }}" \
-e ${{ vars.LICENSIGHT_URL }} \
-at ${{ secrets.LICENSIGHT_ACCESS_TOKEN }} \
-b ${{ github.ref_name }}
GitHub Actions result:
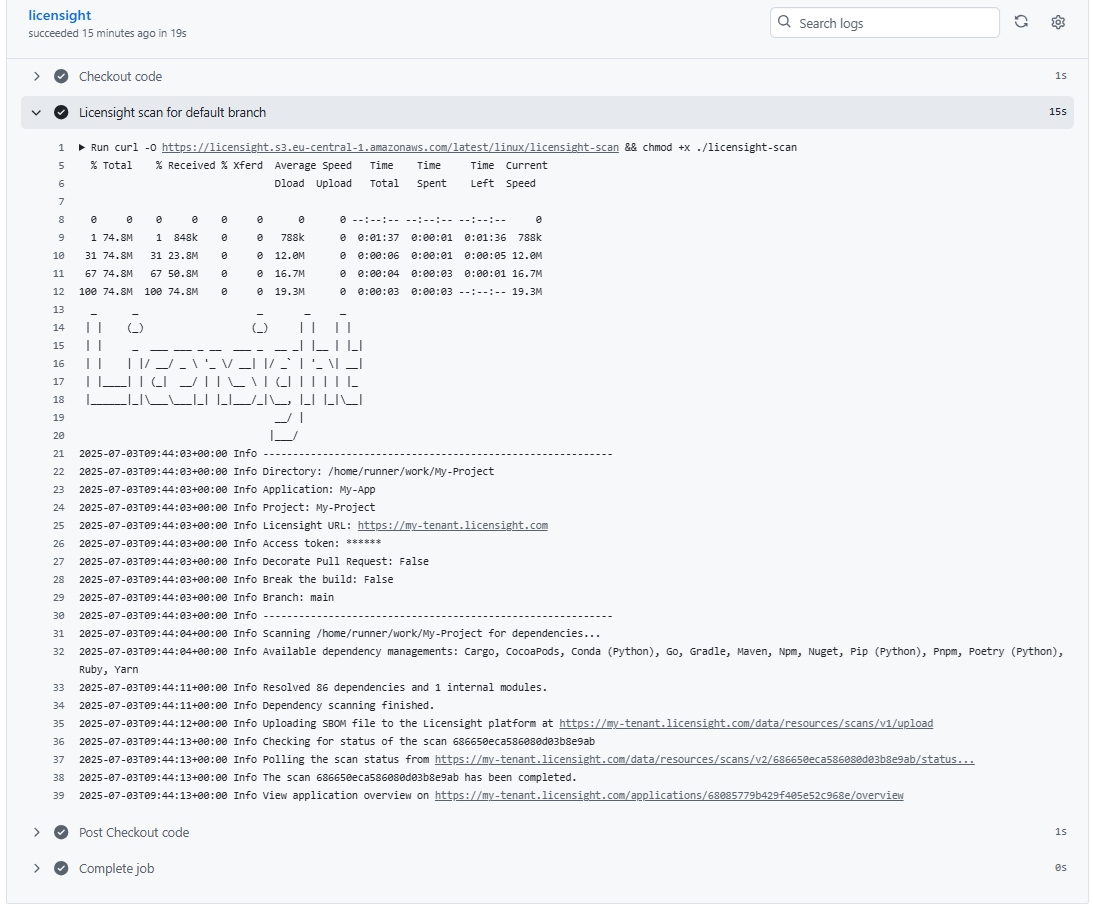
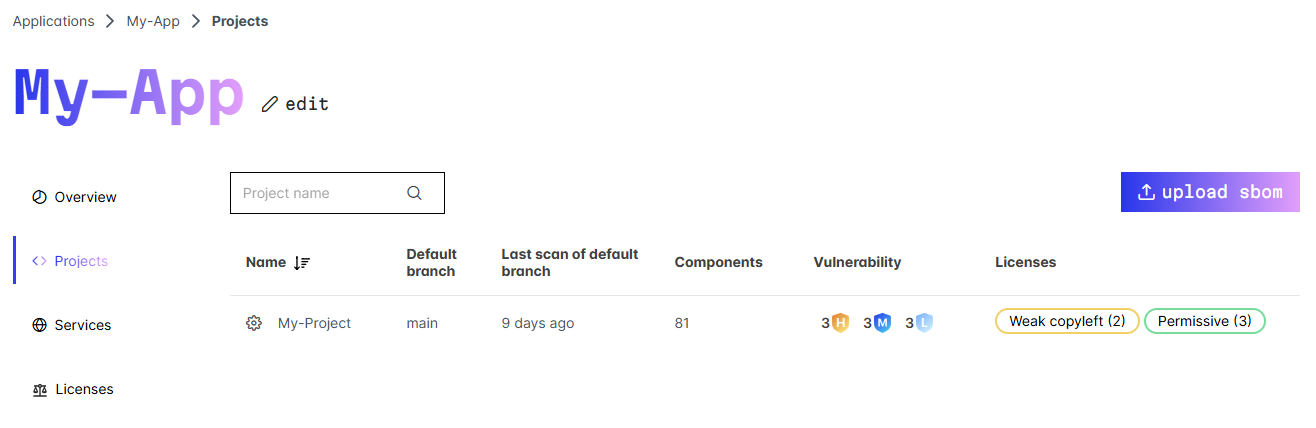
Example for default branch has been scanned:
Scan on Release Tags¶
This GitHub Actions below trigger Licensight every time release tags created:
name: scan
on:
push:
tags:
- "*"
jobs:
licensight:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v4
- name: Licensight scan for tag
run: |
curl -O https://licensight.s3.eu-central-1.amazonaws.com/latest/linux/licensight-scan
chmod +x ./licensight-scan
./licensight-scan generate \
-d . \
-a "${{ vars.LICENSIGHT_APPLICATION_NAME }}" \
-e ${{ vars.LICENSIGHT_URL }} \
-at ${{ secrets.LICENSIGHT_ACCESS_TOKEN }} \
-t ${{ github.ref_name }}
GitHub Actions result:
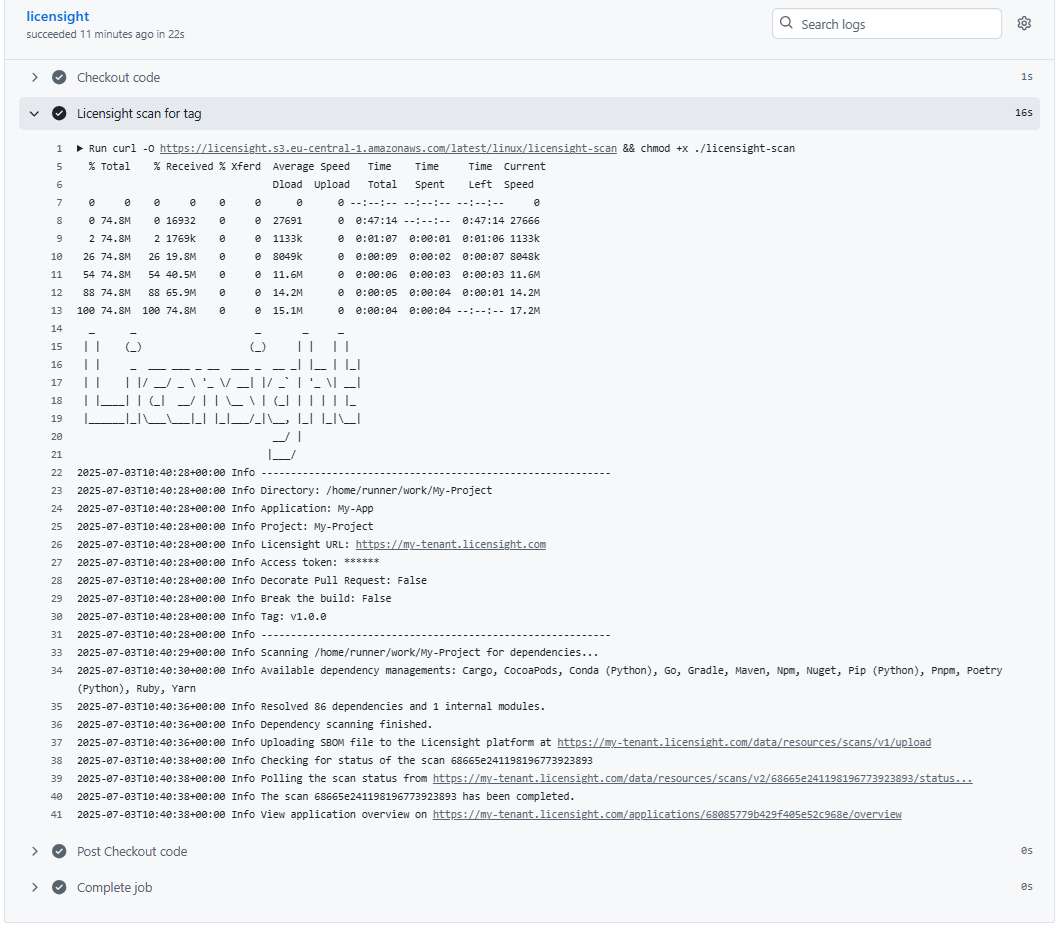
Troubleshooting Common Issues¶
| Issue | Description | Solution |
|---|---|---|
| Exit code 3 | A space in the application name (e.g., My App) is interpreted as two arguments | Wrap the value in quotes: -a "My App" |
| Invalid access token | LICENSIGHT_ACCESS_TOKEN is incorrect or missing |
Check token in GitHub Secrets and ensure it’s valid |
| Unauthorized access to application | You do not have permission to access the Licensight application. | Contact the application's owner to request access rights |
| Scan results not visible in Licensight platform |
|
|
| Private dependencies not resolved | Licensight can't access private repos | Configure credentials (e.g., Maven settings.xml) in the Github Actions |
| Error: No dependencies found |
|
|
| Error happened while decorating the Github Pull Request | GITHUB_TOKEN lacks sufficient permissions |
Go to: Settings > Actions > General > Workflow permissions > Select Read and write permissions > Save |